On our site there are a lot of materials and instructions on how to hack WIFI networks in order to check their security. In the vast majority of cases, we familiarized you with the tools of warriing based on Kali Linux . But to date, the popularity of the Android platform and its flexibility could not but affect the development of tools for hacking WIFI networks using Android.
It's not always possible to test for penetration from a computer, for example, you need to be more mobile or disguised, then a smartphone with tools not inferior to the capabilities of Kali Linux comes to the rescue .
First, let's try to hack a network with the WPS ( Wi-Fi Protected Setup ) enabled . How to hack Wi-Fi with a PC - Reaver . Wi-Fi hacking with WPS enabled
WPS is designed to simplify the connection to a Wi-Fi network , but this standard has a vulnerability. The vulnerability lies in the fact that the attacker can get information about the correctness of parts of the PIN code (the first part consists of four characters, the second of three) and if you take into account that the eighth character of the PIN code is the checksum, then you can derive a formula for calculating all possible PIN-codes:
10 ^ 4 + 10 ^ 3 = 11 000
The simplest defense against this type of attack is disabling WPS in the settings of the router, but the fact is that many users do not even know that they are susceptible to this type of attack.
Currently, many router manufacturers began to make a delay between attempts to search the PIN code from the router ( PIN- code ≠ password from the Wi-Fi network ). But there were many other ways without going through the PIN- code to connect to the wireless network using the WPS protocol .
The last reaver-wps-fork-t6x includes the pixiewps add- in , it allows you to crack most of the routers with WPS enabled without brute-force pin- code .
Well, let's proceed directly to the stress test of our wireless network. All the networks I hacked for this article belong to me.
Open the terminal and move the Wi-Fi adapter to the monitor mode with the command:
That would not do this procedure each time manually enough in the nethunter application in the menu Custom Commands to add this line.
Further through the terminal we enter the command:
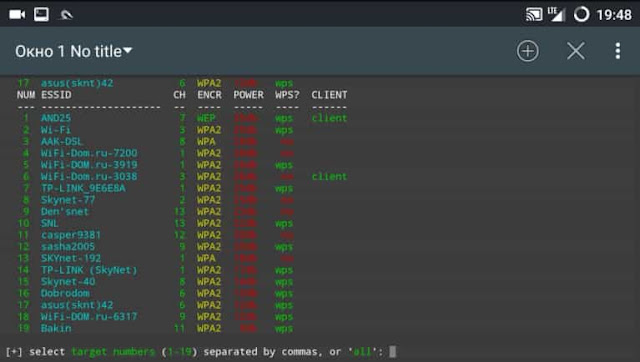
We will wait for scanning and select a network with WPS enabled
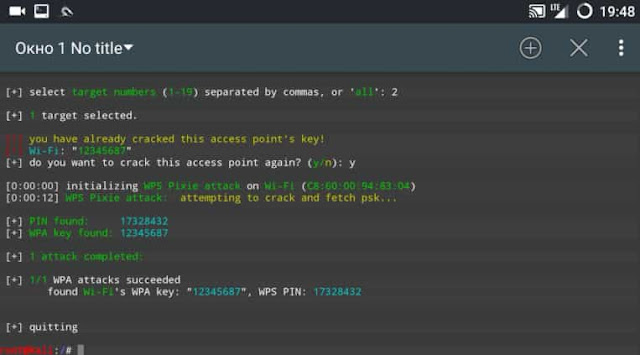
The utility wifite in automatic mode using the pixiewps add- in will try to break the point. .
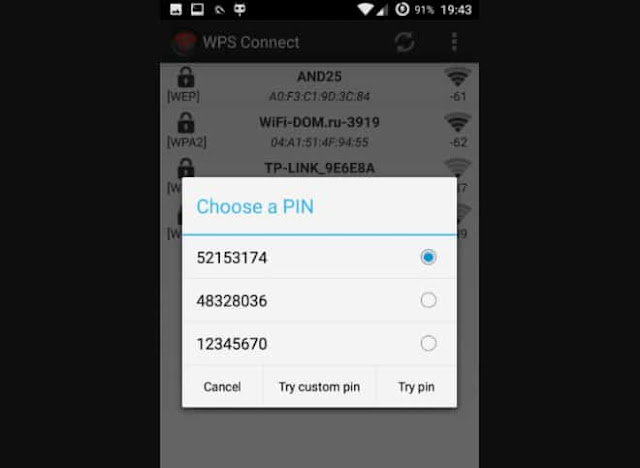
Not all points are subject to pixie dust attack . If the Wi-Fi access point could not be hacked in this way, then you can try the console utility reaver and use the PINCode database. There is a good application for Android " WPS connect " you can download from the " Play market". After starting WPS connect, the application will scan the networks and display the standard PIN codes.
Also, the application will offer to connect using one of the PIN-codes, but this method has the drawback of connecting the application will not be from an external Wi-Fi adapter, but from the built-in phone, which will significantly reduce the connection radius. Therefore, I recommend that you write down the PIN code and use the console utility River. There is also a website that generates a statically PIN-code on the MAC address of the link .
To use the reaver utility, use the command:
Description of the keys:
-I Name of Wi-Fi adapter;
-b MAC address of the point;
-vv a detailed display of the output and errors of the command;
-p PIN code from the WPS connect program or generated using the site.
How to hack WIFI using your Android phone.
Today we will go into more detail about hacking Wifi using the NetHunter distribution , installed on the Android smartphone. About how to install NetHunter on android you can read here.It's not always possible to test for penetration from a computer, for example, you need to be more mobile or disguised, then a smartphone with tools not inferior to the capabilities of Kali Linux comes to the rescue .
First, let's try to hack a network with the WPS ( Wi-Fi Protected Setup ) enabled . How to hack Wi-Fi with a PC - Reaver . Wi-Fi hacking with WPS enabled
WPS is designed to simplify the connection to a Wi-Fi network , but this standard has a vulnerability. The vulnerability lies in the fact that the attacker can get information about the correctness of parts of the PIN code (the first part consists of four characters, the second of three) and if you take into account that the eighth character of the PIN code is the checksum, then you can derive a formula for calculating all possible PIN-codes:
10 ^ 4 + 10 ^ 3 = 11 000
The simplest defense against this type of attack is disabling WPS in the settings of the router, but the fact is that many users do not even know that they are susceptible to this type of attack.
Currently, many router manufacturers began to make a delay between attempts to search the PIN code from the router ( PIN- code ≠ password from the Wi-Fi network ). But there were many other ways without going through the PIN- code to connect to the wireless network using the WPS protocol .
The last reaver-wps-fork-t6x includes the pixiewps add- in , it allows you to crack most of the routers with WPS enabled without brute-force pin- code .
Well, let's proceed directly to the stress test of our wireless network. All the networks I hacked for this article belong to me.
Open the terminal and move the Wi-Fi adapter to the monitor mode with the command:
Ifconfig wlan1 down && iwconfig wlan1 mode monitor && ifconfig wlan1 up
That would not do this procedure each time manually enough in the nethunter application in the menu Custom Commands to add this line.
Further through the terminal we enter the command:
wifite
We will wait for scanning and select a network with WPS enabled
The utility wifite in automatic mode using the pixiewps add- in will try to break the point. .
Not all points are subject to pixie dust attack . If the Wi-Fi access point could not be hacked in this way, then you can try the console utility reaver and use the PINCode database. There is a good application for Android " WPS connect " you can download from the " Play market". After starting WPS connect, the application will scan the networks and display the standard PIN codes.
Also, the application will offer to connect using one of the PIN-codes, but this method has the drawback of connecting the application will not be from an external Wi-Fi adapter, but from the built-in phone, which will significantly reduce the connection radius. Therefore, I recommend that you write down the PIN code and use the console utility River. There is also a website that generates a statically PIN-code on the MAC address of the link .
To use the reaver utility, use the command:
reaver –I wlan1 –b 00:11:22:33:44:55 –vv –p 000000
Description of the keys:
-I Name of Wi-Fi adapter;
-b MAC address of the point;
-vv a detailed display of the output and errors of the command;
-p PIN code from the WPS connect program or generated using the site.
Baca juga:
Advertisement